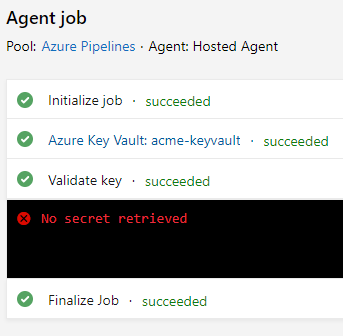
As part of a solid engineering practices one of the first things I flag up during an assessment is how you handle secrets - their management is really one of these things where you cannot cut corners.
Azure KeyVault is awesome in this, as it is really set-and-forget. And using Azure Pipelines with KeyVault is really stuff of the dreams, as the integration between the two makes it really easy to consume.
Let’s say you setup this secret named ‘Key’ in KeyVault:
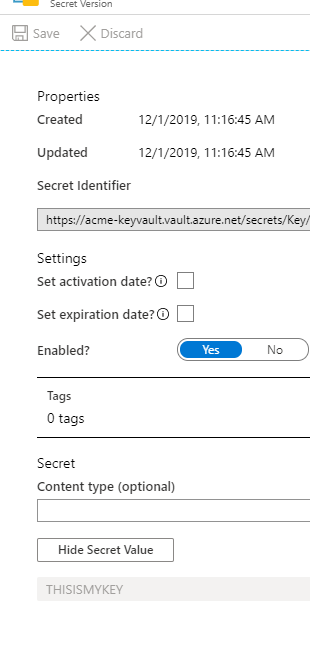
Azure Pipelines and Azure KeyVault by default share a convention over configuration approach, meaning that your secrets’ key names in a KeyVault are automatically mapped to Pipelines variables with the same name. This makes it ridiculously easy to use!
All you need to do is to download the secrets you are interested in from your KeyVault as part of a build or a release, and use the relative variables.
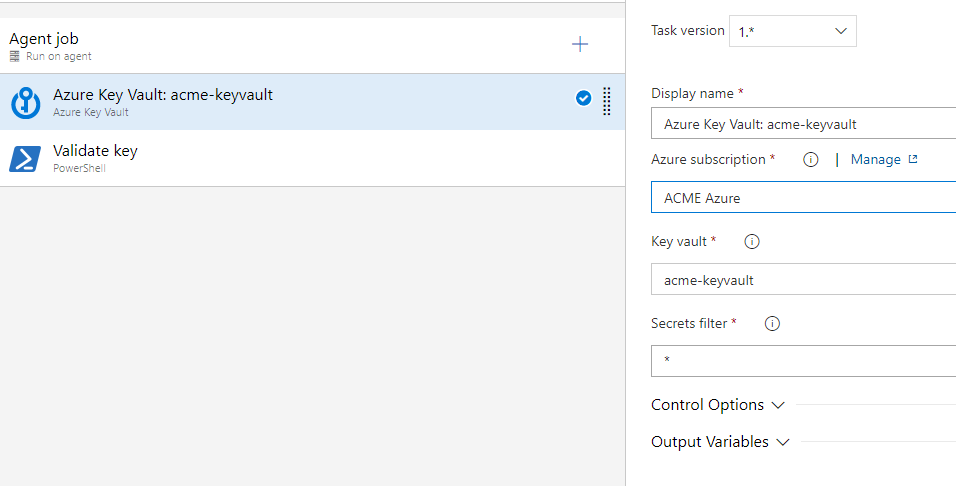
In the real world you would use it to deploy and configure your resources, but I didn’t want to add additional overhead to the scenario - I just want to show you that it works.
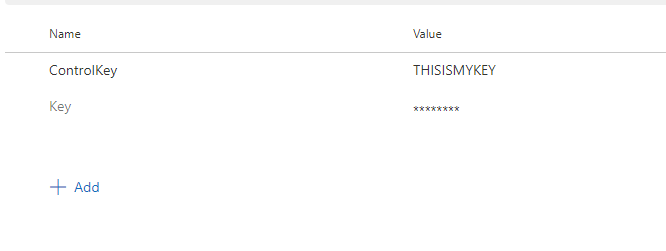
So I created a quick Pipeline that validates a secret with a control value to make sure it is correct - the Key variable is empty but encrypted to mark it a secret, the ControlKey variable is the value against which I want to check it:
Then this barebone PowerShell script is going to validate it on the fly:
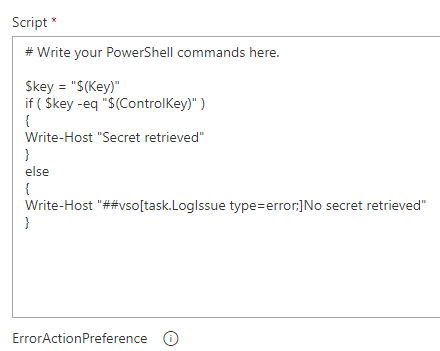
Give it a go, I can guarantee it is going to work as expected :-)